
What Is Cybersecurity?
Learn what cybersecurity is and understand the definitions of different types of threats.

Simply put, a security operations center (SOC – pronounced “sock”) is a team of experts that proactively monitor an organization’s ability to operate securely. Traditionally, a SOC has often been defined as a room where SOC analysts work together. While this is still the case in many organizations, the advent of COVID-19 and other factors has led the SOC team to be more remotely distributed. Increasingly, today’s SOC is less a single room full of people, and more of an essential security function in an organization.
A SOC team member can often function just as well working out of their home office as they can in a physical security operations center.
Members of a SOC team are responsible for a variety of activities, including proactive monitoring, incident response and recovery, remediation activities, compliance, and coordination and context.
Let’s take a deeper dive into each of these tasks.
A SOC team member helps an organization identify the primary causes of cyberattacks. When a SOC analyst does this, they are said to engage in root-cause analysis. In short, a SOC analyst works to figure out exactly when, how and even why an attack was successful.
To this end, a SOC analyst reviews evidence of attacks. Such evidence is called an indicator of attack. If an attack is successful, a SOC analyst will then study indicators of compromise to help the organization respond appropriately, as well as make changes so that similar attacks don’t happen in the future.
Of course, there are several specific positions that round out the SOC. Although specific job roles and titles will change from one organization to another, here are a few of the job titles typically found in a SOC:
First of all, a SOC team gathers information from various resources, including CTI threat feeds to log files from systems all around the enterprise. A SOC team carefully monitors a company’s assets, from on-premise servers in data centers to cloud resources. Accurate monitoring is critical. Therefore, SOC team members will monitor servers, end points and perimeter devices like firewalls and switches.
The figure below provides an abstract view of what happens in a SOC.
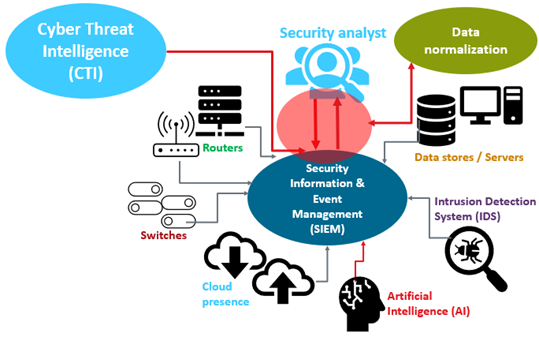
Abstract diagram of a Security Operations Center (SOC)
SOC team members then work to interpret this data carefully so that they have actionable information. Part of this interpretation involves eliminating duplicate data and identifying the root causes of issues. This activity is often called data normalization.
It is not enough to simply view the log files of a SIEM tool. The worker needs to have enough experience and wisdom to interpret data accurately. In many ways, the ideal SOC team member acts as a key interpreter of information.
But the SOC responsibilities don’t end there. The SOC isn’t only charged with looking for the bad guys. SOC team members spend quite a bit of time identifying conditions that create ideal feeding grounds for hackers.
This can include looking for the following:
It is very possible that as a SOC team member you would work closely with managers and end users simply because individuals are the primary target of hackers.
Not everyone in a SOC team has decades of security experience. In fact, some SOC team members have just a few years of experience in IT. Still, others have more.
The primary characteristic of a SOC team member is simply considerable depth and breadth of knowledge in all areas of IT, as summarized in the table below. The skills needed to work in a SOC are covered by CompTIA certifications, as noted below. Having a CompTIA certification proves to employers you have the skills they need in their security operations center.
| Activity | Description | CompTIA Certification |
|---|---|---|
| End point analysis | The ability to understand how a network host is supposed to behave and how it can be manipulated | CompTIA A+ |
| Network and cloud resource evaluation | Experience with how protocols can be misused | CompTIA Network+ CompTIA Cloud+ CompTIA Linux+ CompTIA Server+ |
| Vulnerability recognition and attack recognition | Practical, hands-on experience with exactly what an attack looks like | CompTIA Security+ |
| Analysis of Tactics, Techniques and Procedures (TTPS) and Indicators of Compromise (IoC) | Ability to identify specific hacker activities | CompTIA Security+ CompTIA CySA+ CompTIA PenTest+ |
| Following each step of the hacker lifecycle | Detailed ability to trace how a hacker pivots while making an attack; requires knowledge of various models, including the Lockheed-Martin Cybersecurity Kill Chain, the MITRE ATT&CK model and the diamond model | CompTIA Security+ CompTIA PenTest+ |
It’s important to note that entry-level SOC analysts may not require advanced certifications like CompTIA Cybersecurity Analyst (CySA+), CompTIA PenTest+ or CompTIA Advanced Security Practitioner (CASP+). But the table above should give you an idea of the types of skills SOC analysts, or those who liaise with SOC analysts have.
Learn More About the CompTIA Cybersecurity Career Pathway
If you want a place in the SOC, the best advice is to focus on the essentials. Become an expert on how end points, servers and perimeter devices operate. It’s also vital to understand the cloud and how data flows from one resource to another. Keep studying, and one day we hope to congratulate you as a member of the SOC.
Read more about Cybersecurity.
Tags : Cybersecurity