
What Is Cybersecurity?
Learn what cybersecurity is and understand the definitions of different types of threats.
 It’s safe to say we love our smart devices. Over 24 billion active internet of things (IoT) and operational technology (OT) devices exist today, with billions more projected to exist by 2030.
As individuals, we love how they make our lives more convenient and fun. We can get information in real-time, and stay in touch with each other. They’re essential. Companies love smart IoT devices because they make it possible to stay connected
to consumers and gather information.
It’s safe to say we love our smart devices. Over 24 billion active internet of things (IoT) and operational technology (OT) devices exist today, with billions more projected to exist by 2030.
As individuals, we love how they make our lives more convenient and fun. We can get information in real-time, and stay in touch with each other. They’re essential. Companies love smart IoT devices because they make it possible to stay connected
to consumers and gather information.
Manufacturers, utility companies and supply chain organizations (such as automobile manufacturers, power companies and shipping companies) also love their IoT. This form of IoT, though, is referred to as operational technology (OT).
A term associated with OT is industrial control system (ICS). Industrial control systems include devices and networking capability that allows robots, wind turbines and container ships to operate efficiently. If an IoT device is used to control a physical system, such as an element in the power grid or a device on the factory floor, it is said to be an OT device.
The problem is, cybercriminals love IoT and OT devices, too. Maybe even more than we do. The major issue with IoT and ICS devices is that they make it possible for an individual or company to conduct new and different cyberattacks. Hackers will find malicious ways to interfere with the operations of a company, city or even country.
Cybersecurity professionals often refer to this fact by saying that IoT increases the attack surface that hackers can exploit. Security professionals know this and are the ones who help manage the resulting security risks.
IoT and ICS devices are considered end points. In other words, they are devices at the end of a communications chain that starts with a person or robotics device, and ends in cloud platforms and data centers. IoT and ICS devices don’t just appear out of thin air. They are designed, developed and managed, just like any other computer. Figure 1 provides an overview of the elements inside of a typical IoT device.
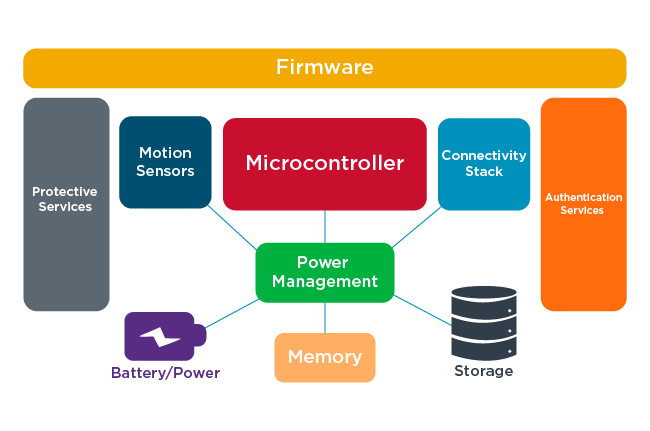
As shown in the graphic above, any IoT device has each of these elements inside:
It doesn’t matter if that device is a webcam, the smartwatch or the Raspberry pi device your local water utility company developed to control devices for your community water supply, the elements remain the same.
Someone needs to develop and maintain each of these elements in order for an IoT/ICS device to work properly and securely. In other words, developers and organizations need to make sure that they create quality hardware and software to run IoT/OT devices. Software and hardware developers work together closely – or sometimes, not so closely, as you’ll see – to make sure that IoT and other computing devices work well with each other.
In fact, there’s an entire IoT ecosystem that exists to create IoT solutions and manage devices. This ecosystem is composed of the elements found in Table 1.
| Element | Description |
|---|---|
| Software developers | The people who develop the software that runs IoT devices. |
| Hardware engineers | The people who create the hardware devices, including processors and microcontrollers. |
| Network connectivity | Service providers, local LANS and mobile networks (including 4G and 5G), are responsible for transporting data and keeping us connected. |
| Platforms | These can include cloud-based services that gather and process the terabytes, petabytes and exabytes of data IoT devices generate. |
| Data analysts and scientists | People who crunch the data from IoT devices and turn it into useful, actionable information. |
| IT workers and managers | Responsible for maintaining the IoT infrastructure, including managing end points as well as IoT network traffic all along the device’s lifecycle. |
| Cybersecurity workers and managers | Individuals responsible for applying IoT security controls, managing cyberthreats and enabling data protection schemes. |
| AI and machine learning | Services often tied to IoT/ICS data to help automate the operation of devices, the collection of data and the processing of data into information. |
Table 1: The IoT Ecosystem
Many times, mistakes or omissions occur as developers create the IoT/ICS hardware and software. No one is perfect.
However, these mistakes can result in the following flaws:
IoT security is one of the major cybersecurity challenges today. Several challenges exist. IoT and OT devices can also provide a rich breeding ground for attackers who want to conduct Distributed Denial of Service (DDoS) attacks, such as through botnets.
A botnet is a large collection of devices that has fallen under the control of a centralized attacker, or group of attackers. A botnet can include tens of thousands, or even millions of devices. Attackers can use these botnets to wage DDoS attacks or introduce malware to new victims. Many of the security breaches that find their way into the news are the results of botnets.
IoT devices can also be used to introduce new forms of malware, which attackers then use to compromise more organizations. Service providers of all types, from cellular network providers to cloud providers and finance companies, continue to be concerned about these security risks.
IoT devices that are not properly developed or secured can result in the conditions found in Table 2.
| Condition | Description |
|---|---|
| Service disruption | Manipulating an IoT device or devices to make an essential service (e.g., a power generating dam, the water system, a database) completely unavailable. |
| Data theft | Gaining improper access to personally identifiable information (PII), such as names, user accounts, social security, national health ID numbers, telephone numbers and residence addresses. Increasingly, organizations and individuals alike are concerned about the use – and misuse – of personal information. |
| Data or service manipulation | Where the attacker can make arbitrary changes to the settings of a device, which can cause loss of life, loss of service, damage to the device itself or damage to other devices. |
| Non-compliance | Governments worldwide have enacted laws designed to protect privacy. Such laws include the European Union General Data Protection Regulation (GDPR) and Health Insurance Portability and Accountability Act (HIPPA), and the California Consumer Privacy Act (CCPA), among many others. |
Table 2: Types of Cybersecurity Threats
As the number and intensity of IoT attacks increases, several notable attacks have been made public. Here are a few examples in Table 3.
| Attack | Description |
|---|---|
| Mirai botnet (Dyn attack) | In 2018, the Mirai botnet created such a large volume of garbage traffic (just over 1 Tbps) that much of the internet was inaccessible in various countries. |
| Stuxnet | In 2010, attackers disabled the centrifuges used in Iran that were being used to create fissile nuclear material. |
| Brickerbot | In 2017, an attack that did more than just clog network traffic or misconfigure devices. This particular attack actually “bricked” the infected device, making it no longer usable. |
| Abbot / St. Jude Hackable Pediatric Pacemakers | In 2017, attackers demonstrated the ability to manipulate the firmware of over 465,000 implanted pacemakers, making it possible to drain the pacemaker battery, steal sensitive data or even change lifesaving settings on the pacemaker itself. |
Table 3: Notable IT Attacks
Additional technological and personnel solutions do exist. Here are a few ways IT professionals can improve their security posture when it comes to IoT devices.
IoT and ICS/OT devices will be in our lives for the foreseeable future. It is up to cybersecurity professionals to make sure that these devices will continue to help us conduct business and enjoy life, rather than be a problem.
Interested in learning more about what it means to become a cybersecurity professional? The CompTIA Cybersecurity Career Pathway can help you identify the essential skills to manage and secure IoT and ICS/OT devices.
Read more about Cybersecurity.