 Cybersecurity as a whole involves any activities, people and technology your organization is using to avoid security incidents, data breaches or loss of critical systems.
It’s how you protect your business from threats and your security systems against digital threats. Although the term gets bandied about casually enough, cybersecurity should absolutely be an integral part of your business operations.
Cybersecurity as a whole involves any activities, people and technology your organization is using to avoid security incidents, data breaches or loss of critical systems.
It’s how you protect your business from threats and your security systems against digital threats. Although the term gets bandied about casually enough, cybersecurity should absolutely be an integral part of your business operations.
In this guide, you’ll find the following:
• Cybersecurity Defined
• Why Is Cybersecurity Important?
• Types of Cybersecurity
• People, Processes and Technology
• Cybersecurity Careers
• Cybersecurity Certifications
• Multi-Layered
Cybersecurity
The CISA (Cybersecurity & Infrastructure Security Agency) defines cybersecurity as “the art of protecting networks, devices and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity and availability of information.” Every organization uses some form of information technology (IT)—whether it’s for bookkeeping, tracking of shipments, service delivery, you name it—that data has to be protected. Cybersecurity measures ensure your business remains secure and operational at all times.
Cybersecurity is the technological counterpart of the cape-wearing superhero. Effective cybersecurity swoops in at just the right time to prevent damage to critical systems and keep your organization up and running despite any threats that come its way. (See? Superhero stuff.) If you want to stay in the business of making money—and we know you do—you need cybersecurity.
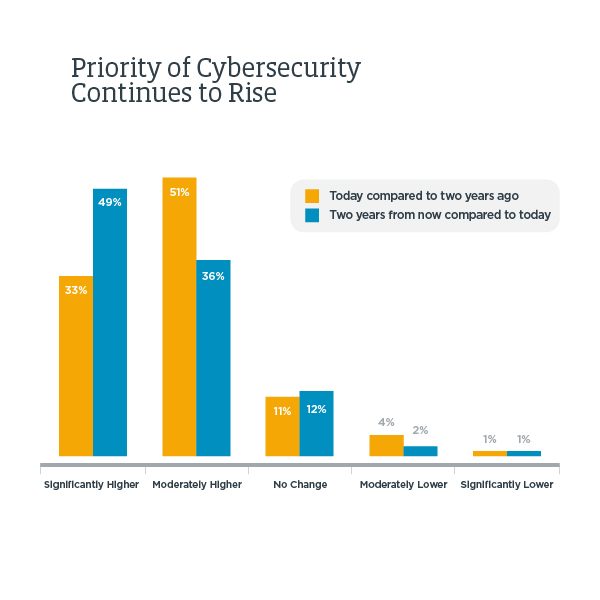
Cybersecurity can mean different things depending on which aspect of technology you’re managing. Here are the categories of cybersecurity that IT pros need to know.
Critical infrastructure security includes the things you do to protect the computer systems your organization needs to stay operational. Seems like a no-brainer, right? This includes any technology, processes, safeguards and other protections you use to keep those critical systems safe and running.
Network security involves all of the activities it takes to protect your network infrastructure. This might involve configuring firewalls, securing VPNs, managing access control or implementing antivirus software. Cybersecurity pros in this field will protect against network threats and data breaches that occur on the network.
Endpoints are any devices connected to your network. This could include desktops, laptops, tablets, mobile devices or smart TVs. Protecting endpoints requires activities such as threat and anomalous activity detection, multi-factor authentication, user training and policy development surrounding endpoint usage. This may also include safeguarding physical locations containing endpoint devices.
Application security involves the configuration of security settings within individual apps to protect them against cyberattacks. This might involve resolving bugs in code and implementing cybersecurity measures to protect against bad actors. Securing applications helps to strengthen data security in the cloud-native era.
Information security includes any data-protection safeguards you put into place. This broad term involves any activities you undertake to ensure personally identifiable information (PII) and other sensitive data remains under lock and key.
Cloud security specifically involves activities needed to prevent attacks on cloud applications and infrastructure. These activities help to ensure all data remains private and secure as its passed between different internet-based applications.
Who over the age (or under) of 18 doesn’t have a mobile device? We all do. Our mobile devices go everywhere with us and are a staple in our daily lives. Mobile security ensures all devices are protected against vulnerabilities. Since we all store sensitive information and use our devices for everything from shopping to sending work emails, mobile security helps to keep device data secure and away from cybercriminals. There’s no telling how threat actors might use identity theft as another weapon in their arsenal!
Internet of things security includes all the ways you protect information being passed between connected devices. As more and more IoT devices are being used in the cloud-native era, more stringent security protocols are necessary to ensure data isn’t compromised as its being shared between IoT. IoT security keeps the IoT ecosystem safeguarded at all times.
Zero trust is a cybersecurity strategy where every user is verified and every connection is authorized. No one is given access to resources by default. Under this model, cybersecurity pros require verification from every source regardless of their position inside or outside the network perimeter. This requires implementing strict access controls and policies to help limit vulnerabilities.
Your people are an indispensable asset while simultaneously being a weak link in the cybersecurity chain. In fact, human error is responsible for 95% breaches. Organizations spend so much time making sure that technology is secure when there remains a sore lack of preparing employees for cyber incidents and the threats of social engineering (see more below). Most often, end users aren’t threat actors—they just lack the necessary training and education to understand the implications of their actions.
Here are six ways that humans contribute to your cybersecurity risk:
Fraudulent emails and malicious URLs. Threat actors are talented and one of the avenues where they see a lot of success tricking employees involves malicious URL links and illegitimate emails. Training can go a long way toward helping your people identify fraudulent emails and links. Teach them to identify red flags such as emails with no content, emails originating from unidentifiable senders, spoofed addresses and messages soliciting personal or sensitive information. Also, encourage immediate reporting of any discovered attempts to limit the risk to others.
Insecure and infrequently updated passwords. We all have our go-to passwords. Maybe it includes your children’s name, your dog’s birthday or an anniversary. Either way, it’s time to ditch overused passwords. Not only should you be regularly updating passwords, but you need to educate users to choose strong passwords. And rather than sticking them on a sticky note in plain sight, consider using a secure password management tool.
Misdelivery of sensitive information. If you’ve ever received an email by mistake, you certainly aren’t alone. Email providers make suggestions about who they think should be included on an email and humans sometimes unwittingly send sensitive information to the wrong recipients. Making sure that all messages contain the right people can limit this error.
Unintentionally sharing PII. In the era of remote work, it can be difficult to keep the lines from blurring between our professional and personal lives. Instruct your employees not to shop on work devices and limit oversharing on social media. There’s no telling how that information could be used to compromise company data.
Failing to update devices. If seeing unattended notifications on your device makes you feel very real anxiety, you probably aren’t one of these people. But some of us are really good at ignoring those pesky alerts to update our devices. This can lead to easily avoided vulnerabilities, which you can prevent by simply doing the necessary updates. In fact, the infamous WannaCry ransomware attack targeted a vulnerability in systems that Microsoft had already applied a fix for, but it was able to successfully infiltrate devices that hadn’t yet been updated.
Lack of physical security. Yes, even if your iPhone locks after two minutes of idleness, that doesn’t mean it’s safe from prying eyes when left in the airport bathroom. Or maybe you typed in a code and a threat actor was peeking over your shoulder. In any case, it’s important that you take physical security seriously and keep tabs on your devices at all times.
Related Content: Security Awareness Training for Employees
Any cybersecurity pro worth their salt knows that processes are the foundation for cyber incident response and mitigation. Cyber threats can be complex, multi-faceted monsters and your processes might just be the dividing line between make or break. Your processes not only outline what steps to take in the event of a security breach, they also define who does what and when.
Outlining clear processes ensures your teams are fully prepped for risk management. When business continuity is threatened, your people can fall back on those documented processes to save time, money and the trust of your customers. Your processes will also help to ensure you remain compliant with governing bodies and meet other stringent regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
Once you’ve got your people and processes in place, it’s time to figure out which technology tools you want to use to protect your computer systems against threats. In the era of cloud-native infrastructure where remote work is now the norm, protecting against threats is a whole new challenge.
Here are some types of tools you may want to include in your toolkit:
• Encryption tools
• Penetration testing
• Network monitoring
• VPNs
• Threat detection
• Firewalls
• Intrusion detection systems (IDS)
• Packet analyzers
• Vulnerability
patching
• Antivirus
• Threat intelligence
• Machine learning/AI threat detection
Cybersecurity threats are continually growing in volume and complexity. The more sophisticated our defenses become, the more advanced cyber threats evolve. While pervasive, cyber threats can still be prevented with robust cyber resilience measures.
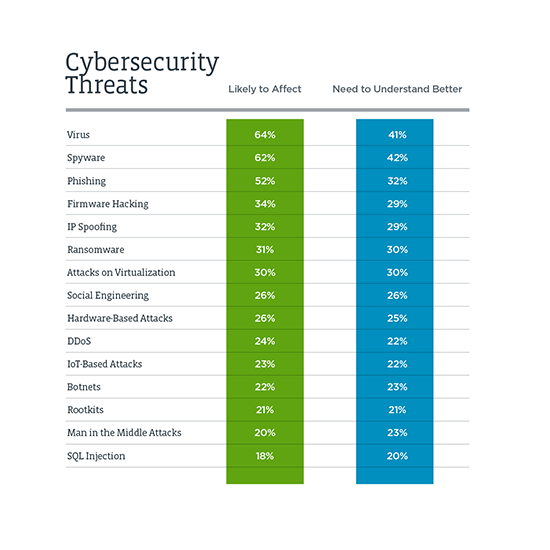
The term malware certainly sounds ominous enough and for good reason. Malware is a term that describes any type of malicious software that is intended to compromise your systems—you know, it’s bad stuff. Malware is most often used to extract information for nefarious purposes or render a system inoperable. Malware can take many forms:
• Virus
• Worms
• Trojans
• Spyware
• Bots
• Ransomware
• Adware
• Rootkits
• Keyloggers
Ransomware doesn’t fare much better in the ominous department, but its name is certainly appropriate. Ransomware is a type of cyberattack that holds your data hostage. As the name implies, nefarious actors will steal or encrypt your data and only return it once you’ve paid their ransom.
Phishing is a type of cyberattack that uses social-engineering tactics to gain access to personal data or sensitive information. Attackers use email, phone calls or text messages under the guise of legitimate entities in an effort to extort information that can be used against their owners, such as credit card numbers, passwords or social security numbers. You definitely don’t want to find yourself hooked on the end of this phishing pole!
Social engineering is a general term used to describe the human flaw in our technology design. Essentially, social engineering is the con, the hoodwink, the hustle of the modern age. When threat actors can’t penetrate a system, they attempt to do it by gaining information from people. This generally involves impersonating a legitimate entity to gain access to PII, which is then used against that individual.
Insider threats are another one of those human problems. Instead of a threat coming from outside of an organization, it comes from within. Threat actors can be nefarious or simply negligent individuals, but the threat comes from someone who already has access to your sensitive data. This threat can also come from vendors, partners or contractors. These are tough to pin down because insider threats originate from a legitimate source that results in a cyber incident.
Distributed denial of service (DDoS) attacks are unique in that they attempt to disrupt normal operations not by stealing, but by inundating computer systems with so much traffic that they become overloaded. The goal of these attacks is to prevent you from operating and accessing your systems.
Advanced persistent threats are those cyber incidents that make the infamous list. They are prolonged, sophisticated attacks conducted by threat actors with an abundance of resources at their disposal. Think attacks on government entities and nation states. These cyber threats often use multiple attack vectors to achieve their objectives.
There are multiple pathways available for cybersecurity careers. Here are some options:
• Cybersecurity specialist
• Cybersecurity analyst
• Penetration tester
• Cybersecurity engineer
• Security architect
• Security operations center (SOC) analyst
• Vulnerability analyst
• Cybersecurity manager
• Security consultant
These are just a few of the roles that currently exist in the cybersecurity sector. As technology evolves so will these roles. That’s why it’s important to consistently keep cybersecurity skills up-to-date. A great way for cybersecurity professionals to do this is by earning IT certifications.
Related Blog: Best Jobs in Cybersecurity for 2024 and How to Get One
Cybersecurity certifications can help advance your knowledge of protecting against security incidents. Here are some of the most popular cybersecurity certifications in the market right now:
CompTIA Security+
CompTIA PenTest+
CompTIA Cybersecurity Analyst (CySA+)
CompTIA SecurityX (formerly CASP+)
Certified Information Security Manager (CISM)
Certified in Risk and Information Systems Control (CRISC)
Certified
Information Systems Auditor (CISA)
Certified Information Systems Security Professional (CISSP)
GIAC Security Expert (GSE)
GIAC Information Security Fundamentals (GISF)
GIAC Penetration Tester (GPEN)
Learn more about how to get into cybersecurity (and other IT fields) on our career roadmap.
A multi-layered security approach secures your data using multiple preventative measures. This method involves implementing security controls at various different points and across all tools and applications to limit the potential of a security incident. Think of it as wearing armor under your bulletproof vest. If something gets through, you’ve got another layer of protection underneath. This approach takes your data protection game up a notch and makes you that much more resilient to whatever comes your way.
Related Blog: A Layered Approach to IT
Read more about Cybersecurity.
Tags : Cybersecurity