Several factors have contributed to this situation. Decades of dropping prices and rising literacy have led to mass awareness and usage of technology. The consumer market is not on par with the enterprise market in terms of revenue, but it receives a large amount of attention. Premium technology is being introduced to consumers, and a working knowledge of these tools does not translate perfectly to enterprise-grade usage.
Growing accessibility has also had a direct impact within the enterprise space. Smaller firms have much more potential to use technology, giving them capabilities that once belonged only to the largest organizations. At those large organizations, technology decisions are no longer confined to the IT team. Business units want to have a stronger voice in the process, sometimes to the point of procuring their own solutions without bringing IT into the picture.
All of this leads to questions for the CIO, IT director, or solution provider. How should the IT organization be structured? What are the fundamental pieces that create complex systems? Which skills are needed to deliver value and vision to the business? CompTIA’s IT framework provides a baseline for answering these questions. By defining the primary pillars of IT, describing the interaction between each functional area, and delineating the skill sets needed, this framework gives IT professionals a template for understanding successful operations and emerging trends.
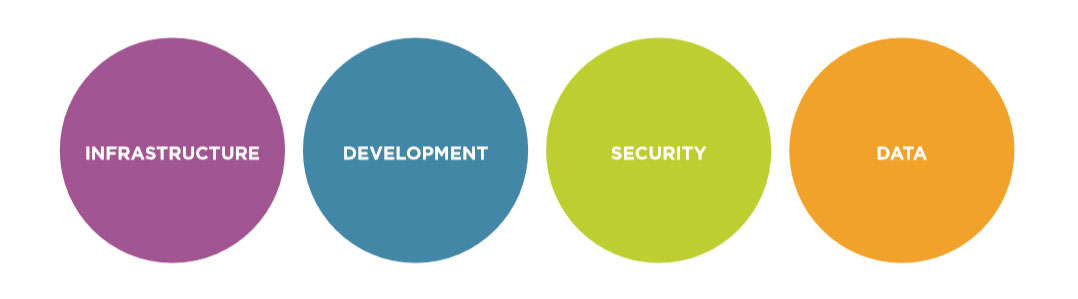
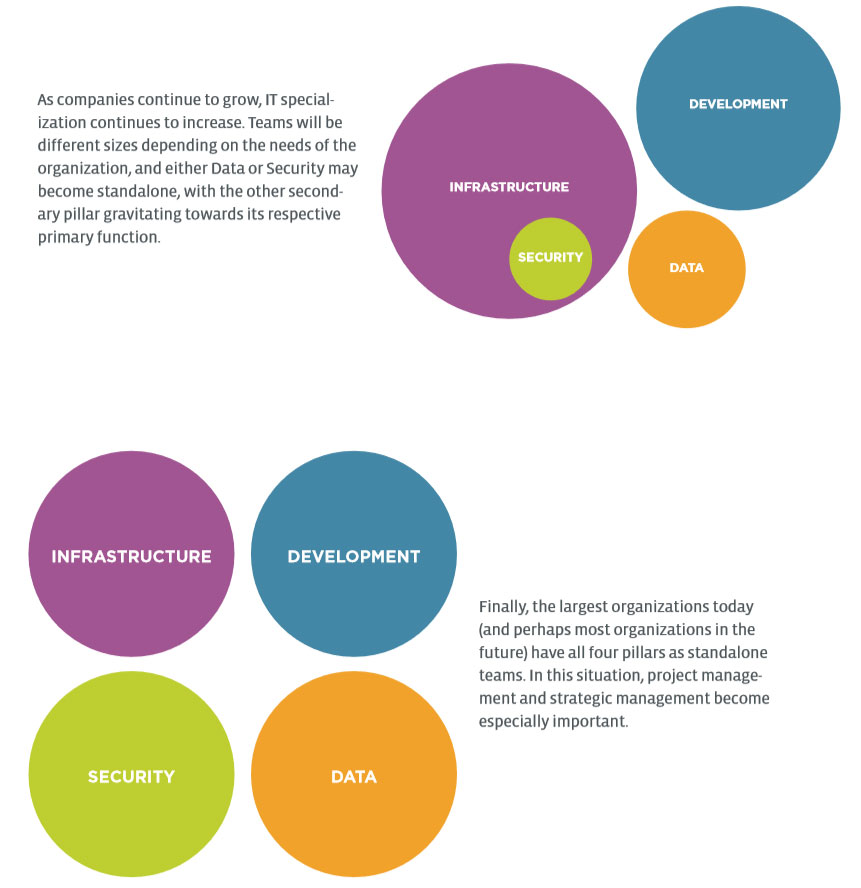
Depending on the size and goals of the business, these four pillars may appear as standalone teams or they may simply be focus areas for the IT group. Where standalone teams do not yet exist, many companies are in the process of creating a team or can envision doing so in the near future. These four areas have long been a part of IT operations, but modern digital organizations are finding that greater competency is needed in each aspect.
At the core of this function, system administrators or network operators perform the back-office tasks that have been part of IT since the mainframe era. Today’s setup requires physical server maintenance, virtual system administration, network configuration, and storage planning. These tasks, which have traditionally centered around on-premise components, establish the foundation for the rest of the IT architecture.
Along with this standard functionality, there are two other significant segments of the Infrastructure pillar. The first is application implementation—while the Infrastructure team does not hold development skills, they are responsible for installing applications and keeping them running. This activity is worth pointing out since it represents a connection point between Infrastructure and Development.
The second segment, which is typically important enough to stand alone in an organization, is help desk or service desk. This first level of support may focus heavily on endpoint devices for end users, but it also acts as the first line of defense for overall infrastructure or application issues. As organizations grow, the help desk becomes a separate function with unique management, but its close ties to the back office and a comprehensive view of equipment to include endpoint devices keep this activity within the Infrastructure pillar.
Several different activities could take place within the Development team. Applications that are used by different business units could be built or customized here. Previously, this activity would have implied a relatively high degree of sophistication within the business and a sizable amount of resources. Increases in technical literacy and broader availability of coding tools have lowered the barriers on both of these constraints, opening internal development to a broader range of companies.
The Internet has also driven development activity. A static online presence is no longer feasible for modern operations; companies use dynamic web tools for daily operations and workflows. Overlap between internal and external activities becomes more common, especially as businesses develop content that is published externally to promote their brand.
Mobility has accelerated this overlap as companies establish their brand in the mobile space. Externally, online offerings must be optimized for mobile devices, whether that means building mobile-friendly web sites or building native mobile apps. Internally, mobile strategies must extend beyond device deployment and management in order to be fully effective. The Development team is responsible for extending desktop and web applications into a mobile world to boost productivity on mobile devices.
As business units shift towards driving more of their own technology initiatives, they may build out their own Development functions. Employees sitting inside non-IT departments will develop applications specifically for that group’s use. As technology becomes more of a democratic process, companies are sorting out the relationships between IT and other lines of business, and determining oversight of siloed development efforts is one part of building a new hierarchical structure
Most companies have long used firewall and antivirus as the means for securing their infrastructure and endpoint devices. For digital organizations, this secure perimeter is not sufficient as applications and data regularly travel outside the walls of the company. New tools such as DLP, IAM, and SIEM must be layered into operations along with firewall and antivirus, and security professionals need to shift their mindset from preventing all attacks to detecting the inevitable breach and acting quickly and decisively.
With business operations heavily relying on technology, having the right processes in place is critical for ongoing success. One example is formal risk analysis, where systems and data are thoroughly reviewed for the proper level of security. This is especially important as companies have less in-house infrastructure behind their own firewall and more outsourced components. Another example is compliance management, ensuring adherence to a growing number of regulations around handling data and conducting digital business. As cybercrime is on the rise across all sectors of the economy, demonstrating best practices is a critical part of maintaining a solid reputation.
The most challenging part of building a secure posture today may be ensuring proper behavior among end users. Companies consistently report that human error is the primary factor in security breaches and data loss, but the resolution is not simple. It primarily relies on education, and most businesses do not have internal education as a core competency. The Security team is responsible for understanding the topics that should be brought to the attention of the general workforce and for delivering education in the formats that will promote a higher degree of security literacy.
Along with the foundation in technology, another characteristic that the Security function shares with Infrastructure is the centralization within an IT team. Business unit professionals recognize that security loopholes are likely when they procure technology on their own, so they attribute responsibility for this area to the IT department. A focused Security function can address each aspect of modern security and develop the metrics needed to show that efforts are successful.
That foundation is the basic management of data, including an understanding of all data throughout an organization and general database proficiency. Many organizations, especially in the SMB space, have data silos where departments have performed their own operations. These silos make overall dataset analysis difficult and lead to a fractured architecture. Similarly, many organizations (again heavily in the SMB space) do not have strong database skills and instead rely on spreadsheets or other simple tools for analysis.
As companies grow in data sophistication, database administrators are needed to efficiently manage the flow of data and perform analysis to draw out business insights. There are many new data management and analysis tools on the market, but the foundation of the Data function uses well-established tools such as relational databases and SQL.
With this foundation in place, companies can move to more advanced tactics. This involves an extension of technical skills into areas such as Hadoop, non-relational databases, and data visualization tools. It also involves a deeper understanding of business practices, since gathering insights from a very large dataset requires some understanding of what the business requires to grow or advance.
Data, like Development, may have outposts within business units. Following the thinking that led to data silos, different departments have different needs for data and may employ their own employees to sift through information and determine a course of action. Again, this brings an organizational challenge as IT determines how to best allow flexibility while maintaining overall corporate guidelines.
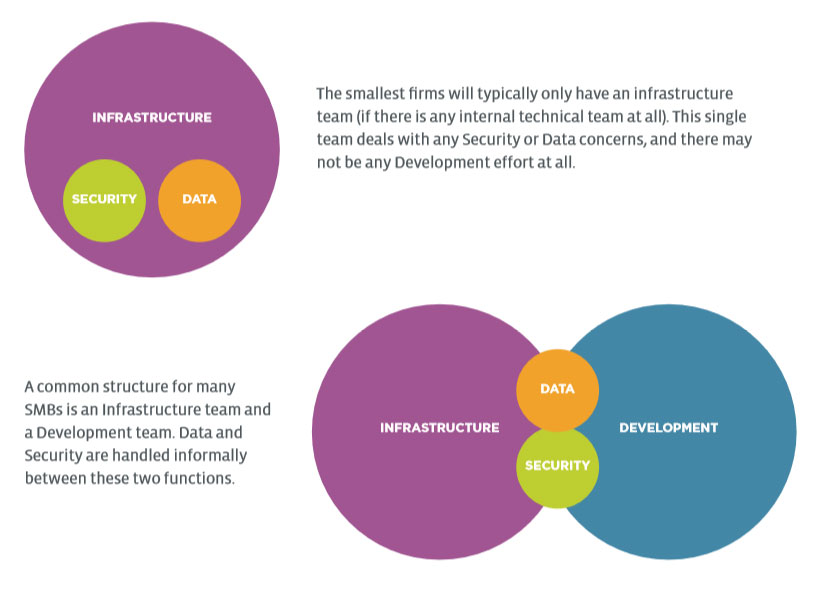
As companies evolve, the team structure around these four pillars will also evolve. Appendix A shows several examples showing how Infrastructure, Development, Security, and Data may be set up within different companies. These examples are illustrative; in practice, each business will have its own flavor. Good IT practices begin with a solid understanding of these four pillars and provide true value by properly managing the overlaps between different areas.
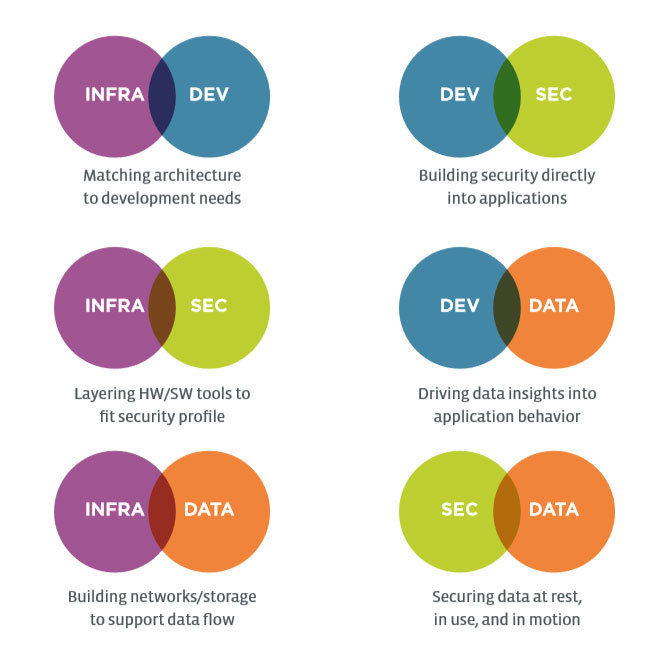
Each pillar represents an IT domain, specifying the ingredients that are used to ultimately deliver business systems. There is some amount of management and tracking with the individual pillars, but the places where they overlap require more formal supervision and control. Several frameworks exist that describe the various components of IT service management (ITIL is the most common example), but at a very high level this is a project management activity.
Project management is present in some form in nearly every IT department. In some cases, it may reside directly within IT; in other situations, IT may rely on a project management office (PMO) that serves all the departments in an organization. Either way, there is usually some tracking and control needed to drive projects from specifications to reality.
Viewed in pairs, project management ensures clean handoffs between groups and approval for activities. Infrastructure delivers environments to Development for building, testing, and production. Security makes sure that Data is following corporate guidelines. Data helps Development understand which aspects of an application are working and which are not. It is a simplified view of the overall process, but it highlights the interactions that occur between groups with different skill sets. In reality, all four pillars overlap with each other to different extents depending on the project. Over the long run, the overlap of all four pillars includes prioritization, tradeoffs, and compromise in order to achieve business objectives. This goes beyond project management to become a strategic role. CIOs, CTOs, or IT directors fill this role when there are internal IT departments. Solution providers may fill this role for clients without their own technical team. Technical efforts always come with constraints, and those constraints must be set and managed by someone with an appreciation for overall business goals and a vision for the part technology plays in meeting those goals.
The IT function, then, consists of four primary pillars that define the building blocks along with project management and executive direction to drive the mission forward. The exact tools and tasks within each pillar and the overall potential that can be achieved by combining the domains change over time, as new trends introduce new possibilities.
New trends certainly have an effect on the shape and inner workings of the IT pillars. The Security and Data pillars are becoming standalone units thanks to the exploration of new models. As businesses place more emphasis on their technical initiatives, the balance of insourcing vs. outsourcing may change. Tasks and skills inside each pillar are in constant flux with the addition of new tools.
With all this change, though, new pillars are not being created. IT operations are still generally represented by the four foundational areas of Infrastructure, Development, Security, and Data; and viewing new trends in the context of these four areas and the way they interact is key to understanding the way that new skills and workflows should be established.
Take cloud computing as an example. There has been a great deal of focus on cloud over the past decade, but the hype is probably justified. CompTIA’s research and discussions within the industry support the notion that cloud computing along with mobility are ushering in a new era of enterprise technology, where the behaviors of businesses change thanks to the capabilities from these new models.
As disruptive as it may be, cloud still does not introduce a new function to be managed. Instead, cloud influences the mindset of each pillar and brings a range of new options to the table. Consider the Infrastructure function—with cloud primarily offering a new way of building IT infrastructure, this team has had legitimate concerns over their future prospects. However, most companies that have adopted cloud computing have not reduced IT staff even as the server maintenance workload has decreased. With the introduction of cloud, Infrastructure employees have adopted a new viewpoint. Rather than believing that their job revolves around physical servers, they have realized that their job revolves around workloads. Keeping these workloads running efficiently is a necessary task regardless of the underlying architecture, and these workers can now focus more on workload optimization.
For Development and Data, the new options presented by cloud computing lead to new possibilities. Where it may have previously been cost-prohibitive to set up multiple test environments or build an architecture to hold massive quantities of data, these things are now within reach. This opens the door to novel approaches.
The Security pillar is perhaps the most likely to undergo transformation thanks to cloud computing. The movement of applications and data outside company walls drives demand for new technology. The use of multiple providers leads to the need for a formal evaluation process. And the possibility of business units procuring their own cloud solutions makes education more imperative. Ultimately, cloud is one of the main factors behind the formation of Security as a standalone team.
A similar exercise can be performed for mobility, Internet of Things, artificial intelligence, or any other big topic that is making waves in the IT industry or business in general. Placing these trends within the IT framework provides insight into how existing activities can be reshaped to accommodate new innovation.

An internet search of “top tech job postings” or “top tech jobs in demand” will yield results with many different job titles, but it becomes apparent that these many titles fit easily into the four pillars. The most common roles fit into Development—titles such as Software Engineer, UX Designer, Mobile Designer, or Full Stack Web Developer. Data roles are also in high demand, especially Data Scientist or Data Analyst, but also including Database Administrator. Infrastructure roles do not get as much press, but those occupations are still prominent in most lists, with titles such as Help Desk Analyst, Systems Administrator, or IT Support.
Many lists focusing specifically on job titles do not feature roles that would fit directly into the Security pillar. The reason for this is that Security is still well embedded in the Infrastructure pillar, down to the level of job titles. So workers with a title such as Systems Administrator perform many security-related tasks. (The same is not necessarily true when Data is embedded within Development—it is common to find Database Administrators inside a Development department.) However, when the discussion is around general skills that are in demand, security rises into the mix. As more companies recognize that security demands full-time focus, roles such as Security Specialist, Security Analyst, and Compliance Officer will be seen more often.
It is worth noting that among the many technical categories that are in demand, project management also appears regularly. Sometimes the job description focuses on project management in technical fields, and sometimes the description focuses on project management within specific verticals. Clearly, companies are looking for a degree of IT service management on top of the various skills they are building or hiring.
As companies bring in greater quantities of technical skills, there is a greater need for hierarchy and progression. The most common entry points are found in the primary pillars. Help desk roles are the typical entry level jobs in the Infrastructure pillar, requiring a broad set of basic skills that can lead into more advanced roles in network administration or systems architecture. Junior developers in the Development pillar can likewise advance to senior developers or software architects.
For Security and Data, entry level positions are a little harder to come by. To the extent that these functions were embedded in the respective primary pillars, they represented the more senior end of the spectrum. As databases have become more widely adopted, it has become more common to find college graduates or early career employees with data skills that can start at a more junior level; this situation will accelerate over time and get replicated in the Security pillar as companies build standalone teams.
As employees advance, the need for cross-functional skill grows. Generally, career paths occur within pillars; it is no surprise to see some paths between Infrastructure and Security and some paths between Development and Data, but it is rarer to see paths between Infrastructure and Development. However, the need to understand at least the basics of another pillar is a critical part of leadership roles. Obviously a CIO will need an understanding of all functions to build the best business systems, and this skills overlap is also important for other senior members as organizations grow and complexity rises.
Read more about Data and Analytics, IT Support and Help Desk.