While presenting the results of a security audit to the board of a medium-sized health care company, the lead penetration tester for a third-party security auditing company got a nasty surprise. After providing documentation showing all the potentially sensitive information that was publicly available, one of the board members revealed that the organization had hired a second auditing team, and that their report listed additional resources that the first auditing team missed. The first pen testing team was let go right away.
The moral of this story isn’t necessarily that people make mistakes or that one of the pen testing teams was better than the other. The important message is that organizations are now taking risk management very seriously. Sometimes, organizations act in useful, rational ways that increase maturity and resilience. In other cases, organizations that lack proper communication and processes make snap judgments and jump to conclusions.
Risk management is a term that both IT and security teams employ every day, whether they realize it or not. It is the consistent process of identifying, analyzing, evaluating and treating loss exposures while also observing risk control and resources in efforts to mitigate the adverse effects of loss. It is often a practice that is also employed within IT departments but used for enterprise systems, networks and devices to mitigate potential cyber threats. When security professionals today use the term Governance Risk Management and Compliance, they’re talking about their daily activities. It is vital to mature risk management practices on a continual basis; otherwise, the technologies we use will become nothing more than the “internet of threats.”
With the ever-evolving cyber threat landscape, organizations have to be more diligent than ever to minimize risk while adapting to new challenges. CompTIA has tracked how corporations have been slowly adopting the hybrid, “virtual” workforce, the cloud and zero trust frameworks and best practices. The COVID-19 pandemic only accelerated this trend. Most businesses have rapidly shifted from primarily on-site teams to remote-only or hybrid workforce environments. This shift has created new challenges for IT and cybersecurity workers. It has changed the existing attack surface. As a result, it is necessary for organizations worldwide to re-evaluate how they manage risk today.
In one case, a financial institution realized that they had a malware problem. They approved security training not only for security analysts and server administrators, but also for help desk workers. Following this training, that organization saw a dramatic decrease in malware-based incidents.
All IT pros need to possess risk management skills. Risk management is a primary consideration for most IT job roles, including help desk professionals, network administrators, security analysts and pen testers. Security architects, compliance analysts and many others spend most of their time helping organizations manage risk. Proper risk management across IT teams within organizations can reduce and prevent cybersecurity breaches and attacks from happening in the first place.
This guide will navigate you through the basics of IT risk management, its types, why it’s so important, how it intertwines with cybersecurity compliance, best practices, and how to build and implement a risk management plan within your IT department.
The majority of all risk management, including IT risk management, falls within the best practices represented by the term Governance, Risk and Compliance (GRC). GRC regularly involves more than simply choosing a framework or conducting a single risk management exercise. Accepted GRC practice calls for integrating and rehearsing practical risk management tactics and their initiatives. Implementing a risk management strategy entails creating, implementing and measuring the efficacy of procedures and processes. It also involves considering how your organization identifies and handles risks and legal expectations. These expectations can include financial, technological and human resources, and industry risk or federal regulations.
In one case, a retired British police officer became a GRC officer. This particular individual never considered himself particularly technical. But, he was very good at obtaining and evaluating information. Furthermore, this individual was also very good at identifying inconsistencies and potential root causes of problems. Organizations value individuals who can do more than consult a list of rules; they need individuals who can identify problems, and then propose solutions.
Many compliance, governance and business risk management teams approach risk management with the goal of following a formula that focuses on a five-step process. This process focuses on risk assessment and mitigation goals in order to meet optimal compliance. It also includes identifying the risks, conducting risk analysis or assessment activities, prioritizing them, responding to the risk and monitoring its threat potential.
While this common five-step process can help ensure compliance, the way teams approach risk management from a business standpoint does not always translate into the same methodology of how IT risk management for cybersecurity is approached. This is often a common issue across enterprises when approaching business risk versus cybersecurity risk.
Cybersecurity often requires IT pros and leaders to look within the deeper root causes of their increased IT risk management. Below are some of the common root causes for IT risk management issues.
Organizations are increasingly moving to source technology solutions independent of the IT department. Whether it be for cost-efficiency or to boost resources, enterprises are utilizing more third-party IT solutions to essentially shadow their IT. Shadowing IT from third-party solutions can aid a department in sourcing a technical solution right away.
While third-party IT solutions can be beneficial, they can also be detrimental to an organization. In one recent case, a research department created a data lake using a popular cloud company to help complete a project. The issue derived from the fact that no one outside of the research department knew this resource was being used nor existed. That led to the third-party cloud company not being properly configured, and an attacker was able to exploit the entire organization by exploiting a security misconfiguration in the data lake. Proper IT risk management instills processes that require all technologies, including third-party technologies, to be identified within an organization.
Security involves more than just external threats and insider threats. It also involves the processes, and the people, used to create technical solutions. Security workers are often tasked with the mitigation of incidents rather than ensuring the processes in place are protecting the enterprise from risk.
Technical debt is what happens when a device or piece of software is created, and a person or organization consciously (or even unconsciously) decides to skip certain steps or use an older set of resources out of necessity. Within IT risk management, technical debt can take many forms, including skipping critical risk management steps, processes and testing. Often teams that resort to technical debt practices do so because of time or cost constraints. IT teams then anticipate the debt will be repaid down the road by skipping steps.
Lack of communication between IT and leadership is often a common risk management issue. Proper risk management is dependent on process maturity, which can only occur when organizational leaders are communicating properly about risk. Take the example of a C-level security executive at a large U.S. retailer. In his previous job, he found that communication was acceptable, but not ideal. He felt that he wasn’t able to discuss processes and needed changes as freely as he wished. So, he moved from managing security at a tech company to a retail organization. The primary reason he took that new job was because he saw the potential for strong communication with his co-workers.
Years later, after considerable success managing risk, he found that his job was much easier because he had the opportunity to understand exactly how people in that organization communicated. His style fit with theirs. As a result, he was able to create relevant risk assessment and risk mitigation goals. It was then, and only then, that his deep understanding of how to use red and blue teams became truly useful. Communication, therefore, helps organizations ensure that technical measures are properly used, according to clearly defined needs and goals. This communication is made possible by management.
But properly monitoring risk means doing more than regularly communicating with management. Executives and security operation center (SOC) teams need to understand the processes that are in place within IT and how they work to manage risk.
If teams aren’t communicating effectively with each other, it can create a false sense of security and therefore create the potential for greater risk. Yes, there are always automated approaches, such as Content Disarm and Reconstruction (CDR), which is a set of technologies that help strip suspect code and data as it enters and exits an organization’s network. But, no technical element, including SOC analysis or automation, can work well unless you have proper communication. That’s what sets mature organizations apart from less mature organizations.
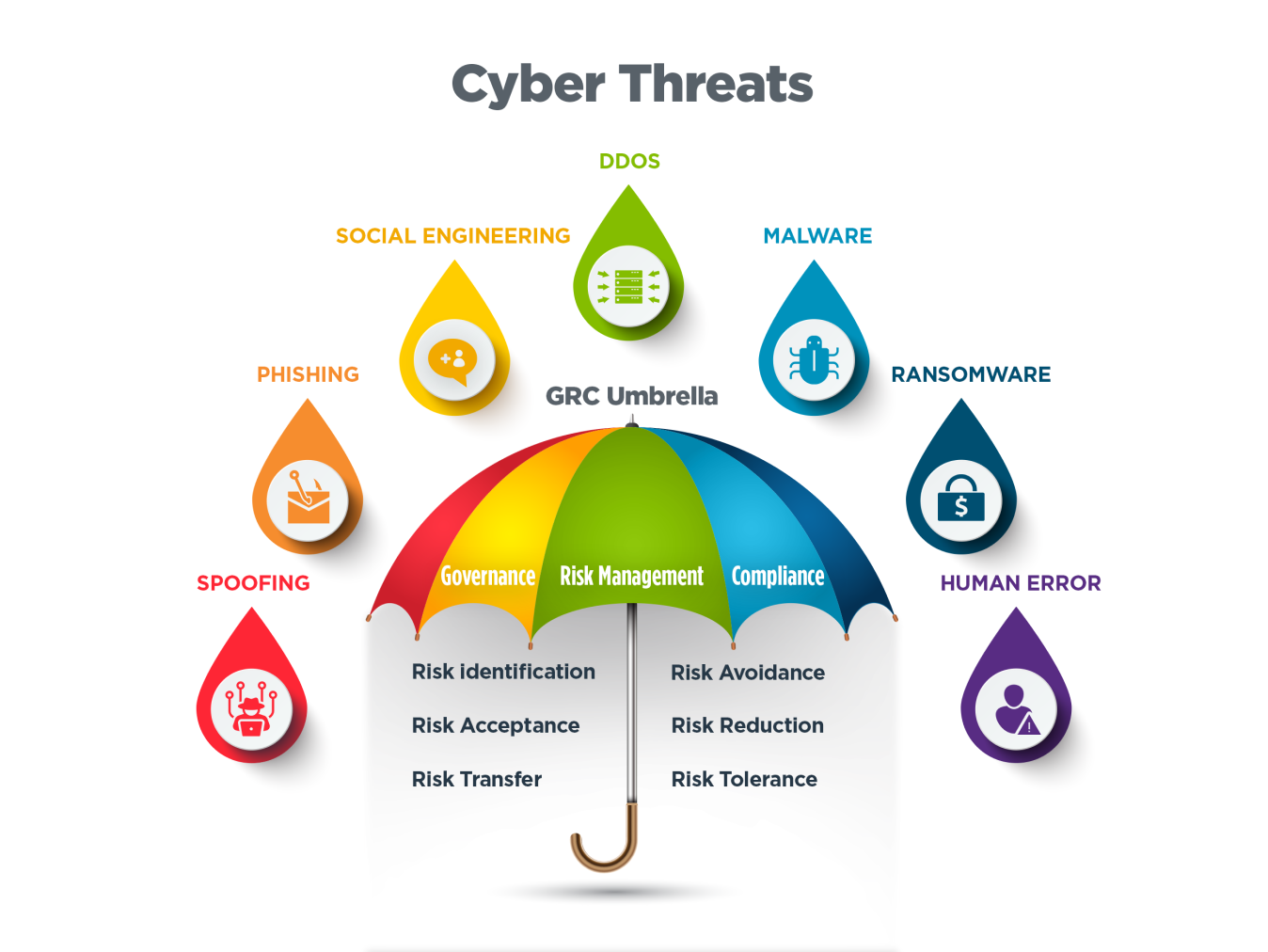
Due to the factors listed above, organizations have largely ignored GRC-based approaches in their risk management practices. Although it may not be intentional, they allow their technology or immediate needs to get in the way of properly managing risk. The result is increased threats and cyberattacks. Social engineering, DDoS, phishing and malware attacks have become more common and destructive because of the lack of practical IT risk management.
Organizations have spent billions worldwide on technological solutions to aid their risk. Businesses are aware of the various threats they face. Yet many organizations haven’t matured their processes to better reduce their risk. Instead of focusing on a technology-first approach, organizations must first focus on a GRC-based mindset to improve their security posture.
Organizational executives and IT leaders alike seem to be aware that they have effectively put the technological cart before the horse, as it were. They know that proper risk management can reduce and prevent cybersecurity breaches and attacks from happening in the first place. Yet the majority of organizations cannot seem to get to the bottom of how to change their ways.
In 2021, Ernst & Young conducted a global board risk survey and found that 57% of risk leaders indicated their teams are only moderately effective at aligning risk and business strategy. The issue is that risk managers are often not aligned with the board and CEOs regarding their business’s greatest strategic opportunities, as well as their associated technical vulnerabilities. Many organizations frequently avoid discussing the problem and instead focus on quick-fix solutions for security. Leaders often tell IT and security teams to buy security to fix the issue or just “patch the system or application.” They often won’t invest in upgrading systems and processes to streamline compliance, security and risk management confidence.
Many companies were not prepared to go fully remote in 2020 and were forced to quickly modify their IT security stature and risk management practices. Respectively, approximately 58 % of risk managers responded to a survey from the Risk Management Institute stating that their organization had not given any consideration to a level of risk similar to a pandemic. These organizations are not risk averse, but rather have an aversion to discussing risk in a meaningful and practical way.
Organizations are increasingly forced into compliance for legal reasons. Laws have sprung up worldwide meant to help manage privacy and cyber theft issues that affect people’s lives and global businesses. IT compliance is best defined as the actions or facts of complying with a regulation to reduce risk in an organization. Teams often are required to uphold cybersecurity compliance within their enterprises, given the digital-driven activities most need to maintain their daily operations. These regulations are often high-level guidelines created for specific industries to address specific problems they may face with risk.
Here are a few real-world examples of regulations that can impact IT pros:
Additionally, some of the more recent privacy laws, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), ensure customer data is protected and stored locally to the consumer. That means if you are a U.S.-based company and you have customers in Europe, you must ensure the customer data is stored in Europe and bound by European laws, even though your company is in the United States.
With regular legislative changes to cyber, privacy and data regulations, IT teams must actively work to ensure they comply with the growing number of regulations. Many IT pros and leaders understand that risk management is part of compliance and that when processes are done well, a mature risk management posture often naturally leads to proper governance and compliance.
It is important to understand, however, that compliance in and of itself is only a half measure. An over-simplified approach to compliance can lead to a ticking boxes mentality. The result is that an organization can lull itself into a false sense of security. If you consider the major security incidents that have been made public over the last ten years, you will find that most of the organizations that were attacked had fulfilled the letter of the law when it comes to privacy and security. The real goal of compliance and GRC is to continually improve and mature processes, not simply follow a checklist.
Business executives are often not used to discussing and reviewing risk in technical terms. Most experienced executives understand how to manage risk effectively for their organizations. IT management and professionals often understand the technical elements of risk management. Yet they tend to discuss these elements in technical terms and not in business terms. As a result, executives and IT professionals tend to talk past each other and in disagreement with one another. The reason for this is that they do not take the time to translate terms and ideas with each other to communicate more effectively.
Business leaders and cybersecurity professionals must thoroughly understand that government regulations are often in the best interest of protecting PII and company data from malicious attackers. Within those laws, there are specific security controls, separation of duties and operational objectives that must be met to ensure legal and regulatory compliance. These regulations often dictate high-level security compliance for most of today’s businesses, even if the specific regulations vary per industry.
Security professionals have discussed the concept of separation of duties for decades. By 2010, most organizations still combined their IT and security workers into one team. Most cybersecurity operations and management teams were created after the historic 2013-2014 cybersecurity attacks on Target, Sony and other major organizations that impacted both enterprises and individuals.
By 2015, infrastructure and cybersecurity teams were separated. This is because the industry realized it needed to focus on two main goals: Continuous security monitoring along with vulnerability assessment, and management focused on the main outcome of minimizing risk and avoiding potential attacks.
Since 2020, we’ve seen even further separation. Today, organizations worldwide tend to focus on three major responsibilities:

To accomplish those goals, organizations built new and separate SOC facilities to monitor security and provide metrics. These metrics are designed to help organizations become more mature by altering their processes. Security workers use software tools like security information and event management (SIEM) systems to help them engage in continuous monitoring. Organizations added vulnerability assessment and management workers (plus the software) to help test systems and conduct penetration tests. Combined with security analytics, these steps help mature processes and make organizations more resilient to attacks.
Security controls are broad tasks that must be implemented, such as backing up information systems or encrypting data. The majority of security controls within organizations include ensuring proper access control policies and procedures, access enforcement, separation of duties and least privilege permissions. These controls can also include penetration testing and other system monitoring activities.
Within greater regulatory compliance, there are specifications of those controls depending on the law and industry in which it applies. For example, PCI DSS has more than 50 security controls, HIPAA has more than 100 and FISMA/ NIST has more than 1,000.
It’s important to note that one specific legal regulation can apply across multiple industries. For instance, legislation like HIPAA is designed to protect patient and provider data, but it can cover more than health care as it also applies to HR practices within enterprises.
NIST Special Publication 800-53 outlines common security controls used by industries across the globe. The more cybersecurity controls, the more difficult the regulation will be to implement if IT risk management is focused solely on compliance versus IT risk maturity. Security controls and processes, when done effectively, are critical to ensure global economies function securely, and businesses continue to provide services, maintain our medical systems and protect our national security.
IT departments are breaking into two groups to accommodate the increase in regulations. Cybersecurity is treated separately from the traditional IT infrastructure team due to the separation of duty requirements in nearly all regulations. The cybersecurity team works in a separate SOC.
Although they are separate teams, the cybersecurity and IT infrastructure teams work together to ensure the organization stays within regulatory compliance. Some of this separation of duties include the cybersecurity team's need to identify and assess risk in order to comply with regulations. That task is then assigned to the IT infrastructure team to complete it.
As organizations grow in size and in required regulatory compliance, they need separate cybersecurity from IT infrastructure to ensure better security control checks and balances. This also ensures security controls are implemented, audited and reported to the correct regulatory agency.
Cybersecurity teams will continue to split from traditional IT infrastructure teams to ensure separation of duty requirements in nearly all regulations. In some cases, organizations have their security teams report to a completely different executive than the IT department. In other cases, ensuring an adequate level of communication and separation of duties achieves the same result. The point is, no single entity or individual should be allowed to provide and then secure a service; in many cases, security and maturity will suffer.
For example, a financial institution in Australia once had the IT department and security department reporting through the same individual. As a result of poor communication, the email administrator created a potential security issue when bypassing endpoint security checks on the email service. She was also able to bypass the firewall, which was acting as a traffic bottleneck, because it was underpowered. As a result, pen testers were able to obtain full control over the email server. The fix was relatively easy: The CIO realized that she had to solve a communications and process problem, rather than a mere technical problem. She made sure that the IT team coordinated properly with the security team when resolving performance issues going forward.
The primary regulatory oversight function is most often performed by the chief information security officer (CISO), who is ultimately responsible for the organization’s regulatory compliance. The CISO also works with the board of directors and the cybersecurity team to meet regulatory compliance requirements. Even if an organization doesn’t have a named CISO, the point is that the CISO function is fulfilled. Executive management is always responsible for managing risk strategically. It is up to CISOs and CIOs to ensure that the organization follows risk management processes adequately.
Cybersecurity management teams enforce regulatory compliance through oversight, auditing and management. They also work closely with the cybersecurity operations and IT infrastructure teams to ensure that compliance measures actually help organizations re-think and transform existing processes. By doing this, internal IT audits and security control reviews do more than enforce compliance. They help an organization naturally improve and transform itself through better processes.
These approaches help make the term digital transformation meaningful. For example, a group of pen testers contracting for a large online and brick-and-mortar retail organization
noticed it was following incident response procedures that were ideal for on-premise systems, but the company had migrated many of its systems to software as a service (SaaS) platforms on Amazon Web Services (AWS).
As a result, the company’s incident response procedures were extremely out of date. This mismatch between on-premise incident response and cloud-based incident
response had existed for at least two years. The company still passed compliance audits each year, even with an outdated process. However, a forward-thinking pen testing team looked beyond compliance and auditing to proactively find solutions
to mature the organization’s processes.
By doing this, organizations lower their IT risk with greater visibility of their systems and networks. In the end, companies can move forward with better regulatory compliance, and have more confidence in their processes and controls within the business.
One of the more common ways to improve maturity is to coordinate pen testing (red team) and security monitoring (blue team) activities. The primary purpose of holding a penetration test should not be compliance; it should be to help security analysts improve the organization’s processes and security controls.
There are numerous risk management frameworks that exist today. It’s important to understand that such frameworks represent only the beginning of the GRC maturity process. As you begin improving organizational processes, it can be useful to consult appropriate frameworks, such as those listed below.
| Framework | Description |
|---|---|
| NIST Risk Management Framework (RMF) | Provides a U.S. government-defined process meant to integrate security, privacy and cyber supply chain risk management. The goal is to create a systematic approach that resembles a system development lifecycle. This framework has been adopted worldwide. |
| ISO 27001 & ISO 27002 | These two documents enable organizations of any kind to use security controls to manage the security of assets such as financial information, intellectual property, employee details or information entrusted by third parties. ISO 27001 provides information about industry-accepted security controls. The ISO 27002 document is a supplement that explains best practice suggestions and guidance for implementing the security controls found in ISO 27001. |
| NIST 800-53 | This particular document is aimed at recommending specific security and privacy controls for U.S. federal government agencies. While it does not officially specify controls for national security organizations, it nevertheless is a common resource for both public and private organizations. |
| NIST 800-171 | Originally meant as a companion to NIST 800-53, the 800-171 document is meant to provide organizations, including U.S. federal agencies, with information about how to control unclassified information. Many organizations around the world have adopted this document as a baseline framework for managing risk. |
In some scenarios, governments and corporations around the world will use NIST-based standards, even though they were originally created in the United States. Other organizations globally may focus more on ISO standards as the beginning of their risk management journey.
Certain organizations are also expected to comply systematically with such frameworks. For example, pen testers and security auditors often focus on the security controls and processes listed in these documents. Many companies and organizations within the finance sector - especially banks - also use the NIST Cybersecurity Framework (CSF). These organizations undergo audits to ensure they comply with required government regulations. Nevertheless, many organizations use frameworks as a beginning of solidifying their risk management goal.
But it is very important to understand that the above frameworks only represent the beginning of the risk management process. Security professionals are expected to modify and depart from the above frameworks in many cases, based on the needs of an organization and the risks that organization encounters.
IT risk management is simple to discuss in basic concepts, but most teams need to become more practical about it. Regulatory compliance is important to all risk management practices. It protects both businesses and individuals from malicious attacks. Compliance is often looked at as the bar to achieve within risk management and the overall enterprise GRC. However, some organizations focus more on the compliance aspect of risk management and not as much on the process maturity needed to achieve compliance naturally.
The primary goal of the cybersecurity team is to ensure compliance with security controls established by a regulation to protect an organization. Typically cybersecurity teams are tasked with most of the IT risk management activities, including monitoring
risk by implementing, auditing and reporting on these activities.
In contrast, the primary goal of the leadership team with the enterprise GRC is to ensure the entire organization is minimizing risk and protecting business assets while
also ensuring regulatory compliance. Most leadership teams are business executives first and discuss risk with a business mindset. For compliance to assist with process maturity, both teams need to communicate the risk issues they face with practical
risk management conversations.
For instance, security control patching may be the solution to minimize system vulnerability or in the event of an incident response. However, specific security patching can differ based on the type of industry.
In Supervisory Control and Data Acquisition (SCADA) industries, most of the operations have a 24/7 need. In the event of an incident or vulnerability, business leaders may reinforce a process that halts manufacturing or operations temporarily.
In an industry like SCADA, the system usually cannot be taken offline and patched accordingly without major disruption. Therefore, leaders and IT teams need to manage expectations of the security controls collaboratively to ensure better process
maturity. IT risk management and GRC compliance have to work together to create, implement and establish processes that focus on process maturity to achieve greater compliance.
Building and implementing an IT risk management plan, or a more resilient risk management plan, is critical in today’s digital-driven world. The key goal for building a risk management plan is to write, develop and practice the plan. Practical and
realistic risk management needs to be written and documented, or it will remain only an idea and set of abstract strategies.
The goal should be to put risk management principles to work for the organization. While this is a fundamental
start, teams need to do more than just write procedures down in a security policy. Organizations need to ensure that these plans are part of its “muscle memory.”
Here are 4 steps to build and implement a practical risk management plan that focuses on maturing processes:
Risk looks and feels different across industries. Some industries have more risk than others. However, risk is something that exists in all businesses. It’s important for IT teams and business leadership to work together to identify what common risks their organization faces.
For example, risk identification is going to be different for a small retail shop than it would for a hospital. For a small retail shop, the biggest risk could be an attack on their digital inventory or payment processing system. In contrast, a hospital is going to have more need for secure processes and must understand that they face a digital risk with their customer data and personally identifiable information (PII), health information, email servers, networks, computer systems and more.
If you cannot identify the weakest points of your business infrastructure, then you may find that attackers will gladly aim to exploit those for you. The goal of practical risk management is to know your weak trigger points. Only then can you work to improve processes and mitigate them.
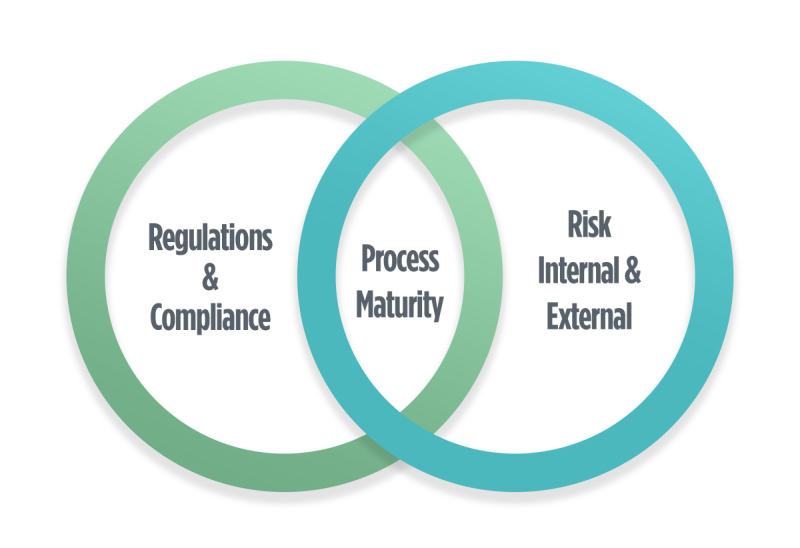
Once the primary risks of the organization have been identified, IT professionals and organizational leaders need to instill practices and processes that aim to evaluate and mitigate that risk. The sweet spot for practical risk management sits in between regulation/compliance/GRC and internal and external risk. This is where businesses need to focus on maturing their processes.
For example, over the past few years, many IT pros and leaders have regularly heard the term “zero trust” shared in regard to risk management. Zero trust is more than just a security term - it’s a process to implement for practical risk management. A zero trust framework views risk as existing on both sides of the firewall. It looks at internal risk as detrimental as external risk.
Zero trust also looks at the processes in place to better secure internal systems as much as external system traffic. Zero trust focuses on processes that require better security plus checks and balances within organizational infrastructures.
For illustration, let’s look at the internal process for your organization of allow-listing or deny-listing. If your organization deals with a lot of controlled data and intellectual property, restricting or securely limiting internal user access to external sites, like social media sites, can minimize the risk of data leaks from your business. It also removes the “good to go” aspect, assuming that risk no longer exists. Zero trust approaches can also help improve internet of things (IoT) and operational technology (OT) security.
IT pros, management and business leadership need to implement better communication across teams. They need to talk to each other, not at each other, and simplify terminology if needed depending on the audience. Conversations should also be more proactive, not reactive.
When building and implementing a risk management plan in an organization, regular risk conversations and communication must be a part of the equation. In today’s constant threat landscape, ignorance is no longer bliss, and risk avoidance only hinders processes - it does not help them.
Organizations have to take the time to review and run risk scenario simulations and exercises. For example, the Target data breach was one of the largest breaches in recent history, and it spearheaded the implementation of better security practices. While some aspects of that breach are still unclear, all it took was one phishing email to unleash an attack that compromised more than 100 million people’s personal information.
For organizations to implement a practical risk management plan, they need to start focusing on activities that run employees and leadership through scenario simulations and exercises. Leadership can create tabletop exercises for IT pros and management to talk through a proposed security incident together and how it can be best rectified. Cybersecurity teams should work with leadership to create full-on activities that involve major portions of the entire organization. Namely, they can run phishing campaigns that send phishing emails to employees to target where there may be a greater risk of incidents in specific departments or teams.
The primary best practice for organizations to effectively manage information risk in IT is to focus on maturing security processes within your organization.
Doing this involves employing organizational activities like the following:
The best practices for practical risk management focus on the processes versus the compliance or GRC demands of the organization. For better risk management, organizations need to shift the risk mindset from avoidance or tolerance to implementing more zero trust within their processes.
Leaders also need to shift the narrative to concentrate their risk management on best practices. They should pivot to increasing organizational resilience rather than compliance. Improving processes requires a strategic approach to IT in order to improve security. Taking a strategic approach to increase resilience is the best way to improve confidence in an organization’s processes.
Education is a critical element in maturing processes and implementing proper risk management within organizations. This is best done through training and education. IT teams and business leadership need to focus on being resilient with their processes which require adapting and evolving knowledge and skills in an ever-changing threat landscape.
For example, let’s explore a real-world scenario of a mid-sized bank in the United States regularly focusing on educating its IT professionals and executives together about risk management. This scenario resulted in executives and IT professionals alike speaking the same language and working together to transform how their company uses technology. Since establishing a greater educational focus, security incidents declined in the first year by 35%.
Global teams can also benefit from more education in order to mature processes. For instance, a large diversified technology company in India began teaching their technical workers how they can better think in terms of business risk management. As a result, they found that help desk technicians, network engineers and others were able to help the organization maintain compliance, but also create new, more efficient processes.
Shifting the focus to maturing processes through better communication and education of both IT and business leadership can create more confidence in processes. More confidence in processes increases organizational resilience instead of solely focusing on compliance with regulations. Cyber threats grow daily, and only through training and education can teams mitigate risk and be able to increase their resiliency from attacks.
Gaining better risk management skills can be critical to helping with maturing processes and implementing better IT risk management for organizations.
Several CompTIA certifications cover regulatory needs, which include IT infrastructure, cybersecurity operations and cybersecurity management. A combination of CompTIA certifications, training and education can help IT pros gain greater skills around risk management.
| IT Risk Basic Concepts | Intermediate Risk Skills | Advanced Risk Skills | |
| Job Roles | Help desk technician/Service desk technician Network administrator Security administrator Linux administrator IT project manager | Penetration tester/Vulnerability assessor Security analyst Data center administrator Cloud administrator | Security architect Senior security engineer Cloud security analyst Data center security analyst Compliance analyst SOC manager CISO |
| CompTIA Certifications | CompTIA A+ CompTIA Network+ CompTIA Security+ CompTIA Linux+ CompTIA Project+ | CompTIA PenTest+ CompTIA Cybersecurity Analyst (CySA+) CompTIA Server+ CompTIA Cloud+ | CompTIA Advanced Security Practitioner (CASP+) |
CompTIA certifications cover IT risk management practices in the following ways:
In many ways, help desk and technical support professionals form the first line of team-based, human defense in an incident. They also help make changes to many organizational systems (e.g., IoT devices, notebook computers, applications, even servers). Therefore, CompTIA A+ teaches incident response procedures, as well as how to bake security directly into applications and devices. CompTIA A+ also teaches change management best practices, including risk analysis, and how to identify the impact, purpose, and scope of a change.
CompTIA Network+ expects candidates to contribute to incident response plans, as well as security policies. This certification also delves deeply into security best practices, including access models, the principle of least privilege, zero trust and threat identification. CompTIA Network+ also requires students to understand how to participate in various types of security risk assessments, including threat and vulnerability assessments.
CompTIA Security+ is the gateway to becoming a security professional. As such, it spends an entire domain on Governance, Risk, and Compliance best practices (14% of the certification). CompTIA Security+ also covers privacy standards that impact cloud security, how to perform systems and security administrator tasks in the cloud, on premises, and in hybrid and heavily regulated environments.
CompTIA Server+ focuses on more than ensuring data center and installed services are available to the “five nines;” Over 25% of the certification focuses on how to implement risk management. For example, Domain 3.0 (Security and Disaster Recovery) teaches students about how to identify data security risks, and how to mitigate specific risks. CompTIA Server+ also helps students understand critical regulatory constraints and legal considerations, as well as how to harden servers so that they present a smaller attack surface.
CompTIA Cloud+ is designed to help workers secure our cloud-first, hybrid world. It therefore devotes at least 25% of its time to security issues, including how to secure a network, enable proper Identity Access Management and how to conduct vulnerability assessments.
CompTIA Linux+ is, in many ways, the key tactical certification for risk management. Linux forms the foundation of virtually every critical service on the internet. Security analysts and penetration testers use Linux extensively. This is one reason why CompTIA Linux+ devotes at least 25% of its time on skills directly related to risk management and security. Skills include secure user management, SSH configuration and an entire domain on security.
CompTIA Cybersecurity Analyst (CySA+) includes a full exam domain on compliance. CompTIA CySA+ helps organizations remain compliant and reduce risk through continuous security monitoring, reporting and incident response, for example.
CompTIA PenTest+ covers penetration testing, vulnerability assessment and management skills to help organizations obtain and remain PCI-DSS compliant, for example. Pen testers are responsible for finding vulnerabilities, or risks, on IT systems; they are an integral part of risk management.
CompTIA Advanced Security Practitioner (CASP+) covers governance and its relationship to security and enterprise network architecture. It includes best practices for standing up sophisticated networks and enabling zero trust principles. A security architect determines how to increase an organizations’ resilience to the next attack, which includes identifying risk, and how to integrate security controls within the existing network architecture to control that risk.
CompTIA offers a full suite of training products to help you learn the technical and professional skills needed to become CompTIA-certified. Find the right combination of the following training products to help you learn the skills you need to get the job you want.
Want to learn more? Download the exam objectives to see exactly what’s covered on each certification exam or start your free trial of CompTIA CertMaster Learn + Labs.