 I’ve been lucky enough to work with information security professionals around the world. Just this week, I was joking with a few CISOs about the many words and phrases we use in our everyday work lives. We talked about the perceived difference between cybersecurity and security and what information assurance and information security mean to various folks at one time or another.
I’ve been lucky enough to work with information security professionals around the world. Just this week, I was joking with a few CISOs about the many words and phrases we use in our everyday work lives. We talked about the perceived difference between cybersecurity and security and what information assurance and information security mean to various folks at one time or another.
Below I’ve listed the phrases that we used as we describe the key job roles and daily activities of a (cyber)security professional. They’re in no particular order, mainly because CISOs, CIOs and hiring managers sometimes use these terms interchangeably.
Words Matter
But words do matter, and we can make sense of them. It’s important to do this, because if we don’t use words consistently, we can end up confusing the people we need to communicate with. So, let’s see if we can figure out the difference between security and cybersecurity, and other terms. I think it starts with information security.
What Is Information Security?
The United States National Institute of Standards and Technology (NIST) Computer Resource Center glossary defines information security as “protecting information and information systems from unauthorized access, use, disclosure, disruption, modification or destruction in order to provide integrity, confidentiality and availability.” This definition is a fairly good starting point, like many things that NIST provides.
Information security is “uber topic,” or a concept that contains several others, including cybersecurity, physical security and privacy. The practice of information security focuses on keeping all data and derived information safe. This includes physical data (e.g., paper, computers) as well as electronic information. In this category, individuals focus on data backups, as well as monitoring techniques to make sure that no one has tampered with data or exfiltrated information.
Sounds reasonable. Years ago, “security” tended to focus on protecting equipment, servers and networks. It has been interesting to see security professionals slowly but inexorably realize that they’re actually in the business of securing information and people.
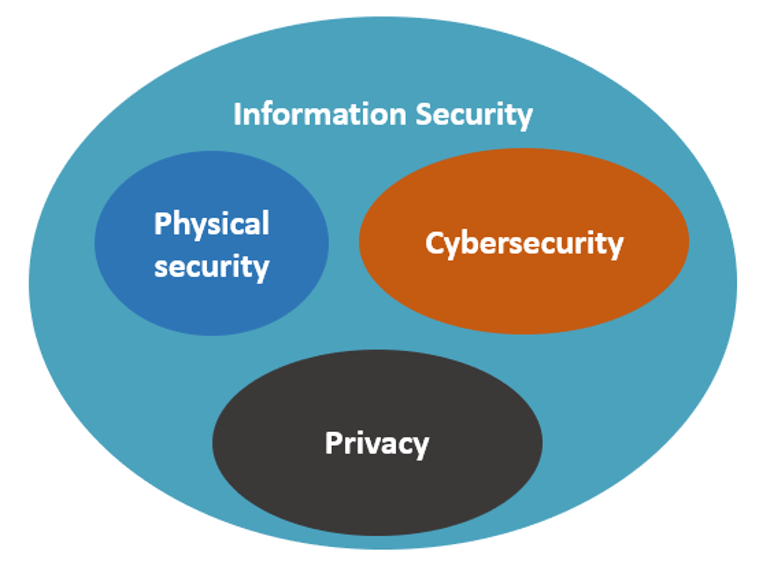
Information security has three sub-categories:
Physical Security
Physical security focuses on how you keep people and physical infrastructure safe. You focus on proper lighting for buildings and parking lots, for example. It also involves understanding how to use camera guards, as well as actual guards and even guard dogs. It also includes securing buildings, server rooms and wiring closets, for example. Some people will use the word security to refer to these physical elements. But the use of security to solely mean “physical security” is hardly universal.
Cybersecurity
To many, this term focuses on electronic assets and resources (including people) used to store and transmit information. The terms “data at rest” and “data in transit” refer to assets such as stored data (e.g., hard disks, S3 buckets, data lakes), operational technology (OT), Internet of Things (IoT) devices and various protocols (e.g., TCP, HTTP/HTTPS).
Cybersecurity tends to focus on the steps malicious actors take against these resources to compromise information in one way or the other. Those individuals interested in cybersecurity are the ones interested in making sure that hackers can’t use electronic means to gain improper access to data and information. In some cases, governments will use the term “information assurance” and cybersecurity interchangeably.
Privacy
The ability to ensure that you have control over how information pertaining to an individual is accessed, handled, disclosed and modified. NIST defines privacy in its 800-29 as “the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification or destruction in order to provide confidentiality, integrity and availability.”
Some would argue that privacy should be considered as an entirely different discipline. This is a valid point. But privacy is so related that it is worth discussing within the context of information security.
Security vs. Cybersecurity: One Way to Discuss It
Even though the terms “security” and “cybersecurity” seem to have unique meanings, folks still kind of mix them up a bit in practice. There’s really no cut-and-dry usage for these terms. I wish there was.
But, maybe it’s possible to use this reality of linguistic confusion as a teachable moment: The most important thing about information security is the ability to create opportunities for people to work together as they protect information and people. Once we all find ways to create common ground – and a common working vocabulary – then we can start making information security a reality. That’s why words matter, and it’s up to us as security professionals to put those words to work.
Get the skills you need for IT security, information security and cybersecurity with the CompTIA Cybersecurity Career Pathway.


0
Job titles and job descriptions vary enormously from organization to organization. It can be called
Job titles and job descriptions vary enormously from organization to organization. It can be called "information assurance," "infosec," "network security," "data loss prevention," and on and on and on and on. There is not a central authority deciding what these terms mean in a job listing.Read full commentThanks for the article, it really enlightens one, on the numerous interchangeability of definitions
Thanks for the article, it really enlightens one, on the numerous interchangeability of definitions and yes, I agree we need a clear understanding of the meaning of each terminology in its own entirety. James, I really like your approach to this article as it keeps it simple - one of the tenets of creativity - hence making it accessible across the board to even non-IT personnel. Thank you for that. I am envious though that you get to dance with CISO's! Thanks for your time.Read full commentIn most cases, cybersecurity is considered an IT job. However, cybersecurity jobs usually focus on p
In most cases, cybersecurity is considered an IT job. However, cybersecurity jobs usually focus on protecting digital information. Some organizations may give these individuals the job title of cybersecurity specialist or cybersecurity manager. Related cybersecurity job titles include cybersecurity engineer or cybersecurity administrator. Although roles and responsibilities may overlap, IT typically has a broader focus on projects, like building and operating computer networks and systems. Cybersecurity focuses on protecting the information within those systems.Read full commentI have to vehemently, but respectfully, disagree with the simplicity of the graphic and discussion.
I have to vehemently, but respectfully, disagree with the simplicity of the graphic and discussion. I could be persuaded to agree if the graphic said, IT Security and had only Cybersecurity in the bubble. No place that I have ever been, and I have been in this business for some time in rolls from Analyst to CISO, has IT Security encompassed Physical and (true) Information Security effectively. I know that there are many organizations, not just CompTIA, who preach that Info Sec, Physical Sec and Cyber belong in IT. This is almost never the case in reality. The skill sets and the influence in the organization is almost never enough in IT to accomplish the goals of real Info Sec, as well as Physical Sec. Cyber can be accomplished in IT for sure. However, when one considers the full gambit of Info Sec, to include GRC, one cannot come to the conclusion in any larger organization, that governance, risk and compliance can be accomplished and overseen in the same organization. That is the near literal fox guarding the hen house. Any significant Info Sec compliance has a tendency to fail when done in a single org, with no oversight. Corners can be cut, winks and nods can be put in place instead of solid evidence of compliance... that is until the toll has to be paid and someone outside the org comes in to verify and validate evidence for compliance. Keep in mind, this is from experience in federal government, insurance, banking, public and private companies, as well as industries with little to no regulation.Read full commentMost people get confused between the terms IT Security and cyber security. This is the reason why I
Most people get confused between the terms IT Security and cyber security. This is the reason why I found this post extremely relevant in the present time. I like the image of sets that you have used to explain IT Security and Cyber security in greater detail. Keep sharing such informative and useful posts.Read full comment