
The topic of information sharing has waxed and waned in popularity over the years. Lately, though, we’ve seen it become quite important. In fact, the new version of CompTIA Cybersecurity Analyst+ (CySA) expects candidates to have a strong understanding of how to use cyber threat data and intelligence sources for threat modeling.
What Is Cyber Threat Intelligence, and Why Is It Important?
I’ve noticed, though, that quite a few folks are still a bit hazy about what cyber threat intelligence and threat modeling really means. Even cybersecurity pros sometimes wonder. This is likely because the topic has been bandied about for a while and has taken a few different forms over time. So, before I go into any details about cyber threat intelligence, let me start with a quick analogy from Major League Baseball (MLB).
In 2017, the Houston Astros baseball team won the MLB World Series after a very impressive season. But in the years since, they have been accused of cheating in a major way: Using the replay technology reserved for MLB officials (e.g., videos and televisions) to steal signs and warn their own batters about the next pitch coming to them.
Stealing signs wasn’t the issue – in baseball, using your wits is expected, and stealing signs through observation is expected. But using technology is against the rules.
According to an MLB investigation report, the Astros used high tech (video monitors) and low tech (literally banging on a garbage can) tactics to warn their batters about the next pitch. One bang on the garbage can meant a fastball. Two meant some sort of off-speed or change-up pitch. You don’t have to be an expert in baseball to know that every hitter would absolutely love to know what type of pitch is coming across the plate!
Baseball Controversies and Cybersecurity: Why Cyber Threat Intelligence Can Be Useful
So, what does all this Astros stuff have to do with threat intelligence sharing and threat profiling? Quite a bit, actually: The Astros supposedly profiled pitchers by stealing signs and then sharing that information with its players about the next pitch – or, in a way, the next big hit. Even if they broke the rules, they had the right idea: Wouldn’t it be nice to see how your opponent is going to attack you?
When it comes to combating hackers, it’s acceptable to profile the tactic, technique and procedure (TTP) that a hacker adopts. We’re seeing the growth of Information Sharing and Analysis Organization (ISAO) entities, including one at CompTIA. And organizations gather and analyze threat intelligence feeds to help them determine from where the next cybersecurity hit will come.
More Free Cybersecurity Tutorials from James Stanger
How to Use the MITRE ATT&CK Navigator for Threat Modeling
One way to figure out where the next hit is coming from is to use the MITRE ATT&CK Navigator, shown in Figure 1, below.
You see, it’s one thing to have a general ransomware plan in case of a cyberattack. That’s a good thing. That might actually put you further ahead than most companies, even today.
But, it’s quite another thing – a much better thing – to have a detailed, tactical, procedural understanding of how to respond to an attack. You see, the promise of cyber threat intelligence is that you can get the blueprint of a response.
The MITRE ATT&CK Navigator in 4 Parts
Imagine if someone worked with the IT industry worldwide to identify the common targets and issues we all face as IT pros?
Enter the MITRE ATT&CK Navigator, which has four parts:
- Pre-ATT&CK: Helps an organization identify areas that could be attacked
- Enterprise: Focuses on key technologies and vulnerabilities in a traditional or cloud environment
- Mobile: Mobile and IoT devices deserve their own category, as they have become a primary attack target
- Industrial Control System (ISC): Devices such as wind turbines and control systems for pipelines and power grids are also a major area of concern
Figure 1: The MITRE ATT&CK Navigator page
Assuming that MITRE’s approach and categories are both accurate, imagine the possibilities. Organizations can now conduct quick calculations to help them anticipate hacker attack strategies and communicate them more clearly to ISAO organizations.
Profiling Hackers In the MITRE ATT&CK Navigator
Using the MITRE ATT&CK Navigator or similar tools, organizations can categorize attacks by specific threat groups and threat actors. It is even possible to profile the technologies and the procedures attackers use. In short, you will have a strong idea of the next move your opponents are going to make.
For example, I went to the Enterprise Navigator and started a new profile. I began with the list of the many technologies that an attacker or threat group could exploit, as shown in Figure 2.
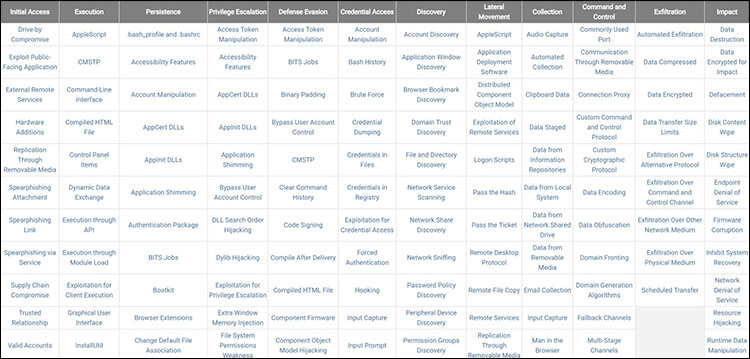
Figure 2: The list of exploitable technologies in the MITRE ATT&CK model
Notice that each of the technologies is categorized into a version of the hacker lifecycle. The top of the page reads Initial access, execution, persistence, privilege escalation and so forth. These are the general steps that attackers take as they compromise a network.
The MITRE ATT&CK Navigator then allows you to profile specific attack groups. Each group profiles an actual group of cyberattackers. Using this model, you can quickly identify how each group operates.
Going back to my baseball analogy, imagine if you knew that a group of pitchers behaved a certain way. Now, you can profile that behavior and train your batters to best address how those pitchers are trying to defeat you.
Using the MITRE ATT&CK Navigator, I selected the FIN6 group as a profile. This group is said to focus on stealing payment card data from the hospitality and retail sectors. I was able to highlight preferred tactics and procedures, as you can see in Figure 3, below.
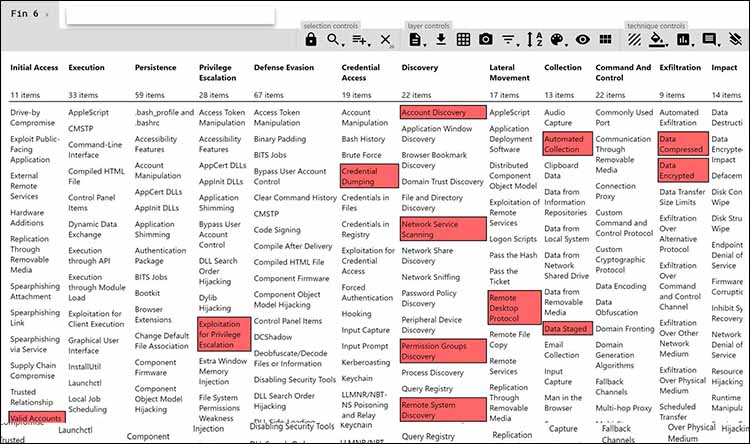
Figure 3: FIN6 tactics, techniques and procedures
Assuming – and it’s a fairly big assumption – that a group similar to FIN6 will try to come after me, I now know their tactics. Instead of worrying about the myriad ways anyone can attack me, I now know how to defend against specific issues.
Contextualizing Cyber Threat Intelligence
Of course, you’d better be sure of your data. What if you prepare for a FIN6-like attack, but the threat group changes its tactics? Information sharing and attack profiling still remains an important, useful approach.
The primary way that organizations keep information relevant is to further contextualize it. One way to do this is to profile additional groups. For example, in Figure 4 below, I’ve profiled not only FIN6, but also FIN7.
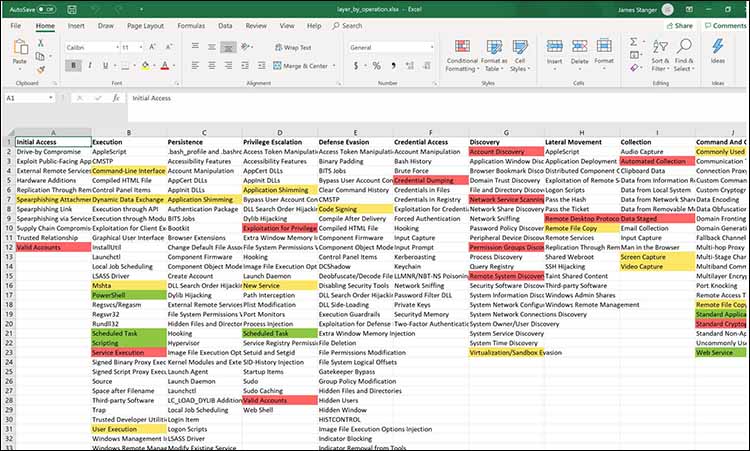
Figure 4: Profiling multiple groups
With this profile, I’ve used the same tools that cybersecurity analysts do to basically say that I think my organization will be attacked by threat actors who behave like the FIN6 and FIN7 groups. I exported the results into a simple spreadsheet:
- The red highlights indicate technologies that the FIN6 group attacks
- The yellow indicates the tech FIN7 groups go after
- The green indicates technologies that both groups seem to favor
With this type of information, it is possible to model specific threats. Now, you can focus your efforts, money and security controls on the green areas – technology that’s most often targeted by the hackers most likely to come after you.
And, if you obtain additional information – from an ISAO or your own research – you can get even more contextualized information. If you store it in your threat intelligence application, such as Yeti, you now have a knowledge base that helps you anticipate the next attack even more intelligently.
Is There a Problem with Threat Modeling?
Of course, nothing is perfect. I think we’ve all seen how an underdog can beat a superior team. That’s why they actually play the games, right?
It’s the same thing with cyber threat intelligence: no prediction is perfect. But, if we get our models correct, then we can take a much more analytical, anticipatory approach to cybersecurity.
Show employers that you have the cyber threat intelligence and threat modeling skills they need with the new CompTIA Cybersecurity Analyst (CySA+). Download the exam objectives for free to see what's covered.




0