
How to Avoid Social Engineering Attacks
Tips to avoid becoming a victim of social engineering attacks.7/13/2022 | Infographic

7/13/2022 | Infographic
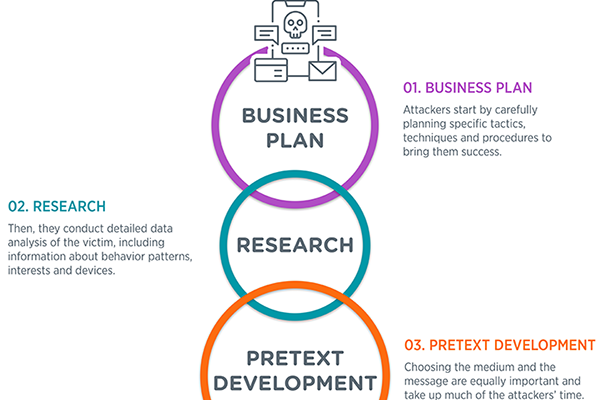
7/12/2022 | Infographic

7/1/2022 | Whitepaper

6/30/2022 | Use Case

6/9/2022 | Research

6/8/2022 | Article

6/3/2022 | Guide

5/23/2022 | Article